Did you know that 80% of account restrictions on platforms like LinkedIn stem from undetected behavioral anomalies, often leading to bans that halt sales outreach overnight? In this article, we'll explore what are account anomaly detection systems, how they safeguard LinkedIn profiles for high-volume B2B operations, and why they're essential for co-founders managing rental services — drawing on real-world insights to help you monitor activity effectively and scale securely.
Understanding Account Anomaly Detection Systems
Account anomaly detection systems are sophisticated tools that monitor user behavior on platforms like LinkedIn to identify unusual patterns signaling fraud, automation abuse, or security threats. By establishing a baseline of "normal" activity — such as login frequency, message volume, and connection requests — these systems flag deviations using rules, statistics, and machine learning.
For instance, they detect login anomalies like impossible travel (e.g., sessions from New York and Singapore within minutes) or activity spikes like sudden 10x increases in outreach, which could indicate bot-like automation. According to IBM's overview on anomaly detection, these systems often employ unsupervised machine learning models, such as clustering algorithms, to spot outliers without predefined labels IBM on Anomaly Detection.
In the context of LinkedIn, where B2B sales teams rely on consistent access, these systems are crucial for preventing restrictions. LinkedIn's own open-sourced tool, ThirdEye, exemplifies this by using real-time analytics on Apache Pinot to monitor metrics and trigger alerts LinkedIn Engineering on ThirdEye.
How Account Anomaly Detection Systems Work
These systems combine multiple techniques for robust monitoring:
- Rule-Based Detection: Enforces hard limits, like daily connection caps, and heuristics for repetitive messaging. For example, if identical templates flood inboxes, flags are raised to curb spam.
- Statistical Methods: Analyze time-series data with tools like z-scores to detect outliers, such as non-human 24/7 activity patterns. NIST guidelines emphasize this for cybersecurity, recommending continuous monitoring in identity management NIST SP 800-53r5.
- Machine Learning Models: Use unsupervised approaches like autoencoders to reconstruct normal behavior and highlight errors, or graph-based models to uncover bot networks through connection patterns.
Expert insight from cybersecurity professionals highlights the evolution: "Spam is now machine-generated. The only effective counter-measure is machine-driven detection," notes a recent analysis in the EU AI Act framework, which promotes risk-based AI for trustworthy systems EU AI Act.
For co-founders overseeing thousands of client accounts, integrating these into your workflow — much like our Single Session LinkedIn Protection — ensures safe scaling without triggering platform alarms. Learn more about our approach at LinkedIn Safety.
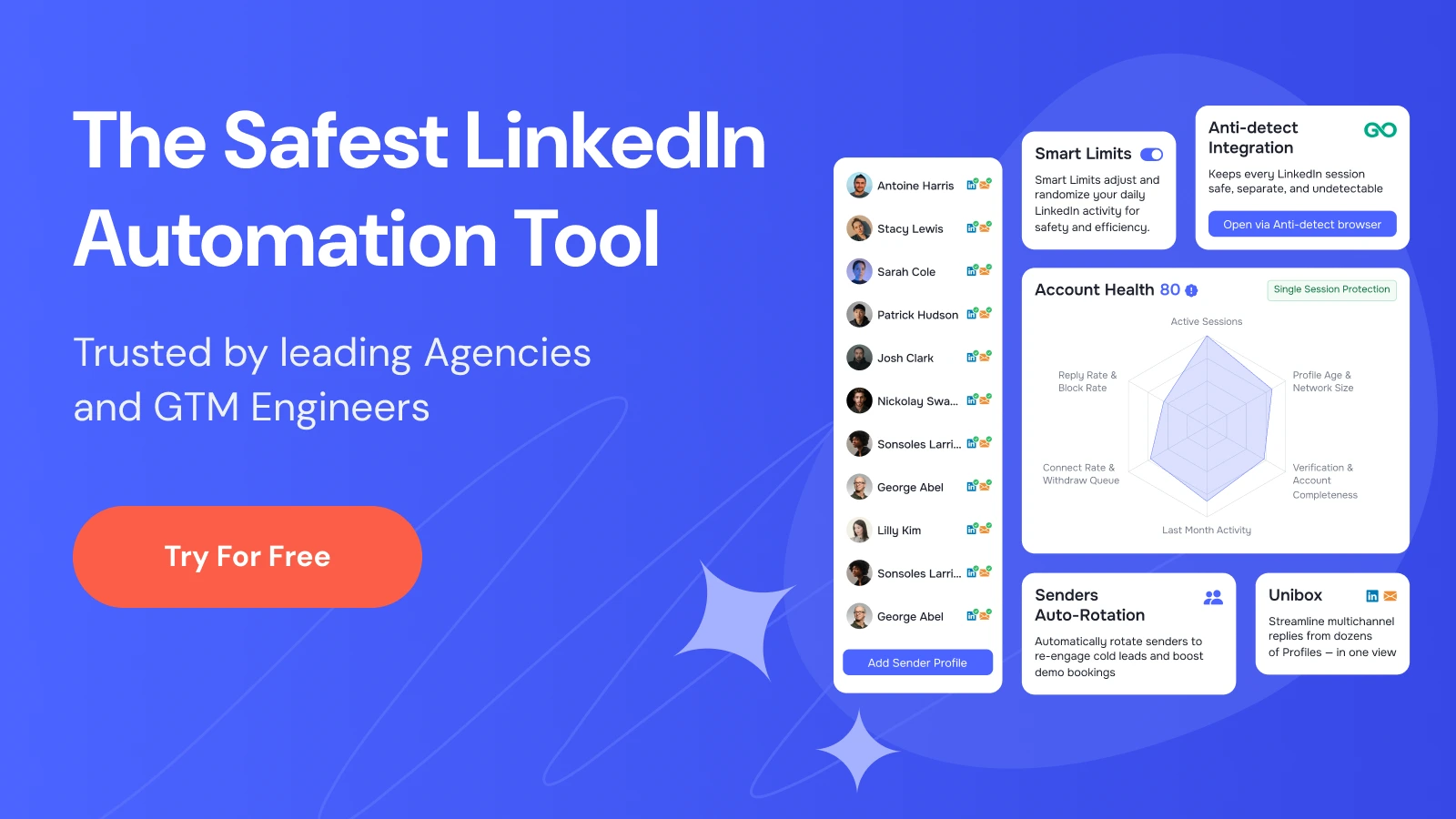

Why These Systems Matter for LinkedIn Profile Management
As co-founders of LinkedIn profile rental services, your job to be done (JTBD) is monitoring account activity for anomalies to maintain security and scalability. Without detection, risks escalate: A single banned account can disrupt client campaigns, leading to 30-50% drops in outreach volume, based on industry reports from sales automation case studies.
Key benefits include:
- Early Compromise Alerts: Spot unauthorized access, reducing takeover risks by up to 70% through proactive flags Forrester Research on Anomaly Detection.
- Compliance and Reputation Protection: Align with LinkedIn policies against unauthorized automation, avoiding fines under regulations like GDPR.
- Operational Continuity: Prevent downtime from restrictions, ensuring steady lead generation.
Recent news underscores the stakes — a 2023 LinkedIn crackdown on automated farms restricted thousands of accounts, per TechCrunch reports TechCrunch on LinkedIn Automation Bans. At GetSales.io, we prioritize this with features like Rotating Sender Profiles to mimic human behavior and minimize anomaly triggers.
Risks of Ignoring Anomalies and Best Practices
Failing to monitor can lead to severe consequences, such as account restrictions from over-automation. For example, agencies using shared IPs often trigger graph anomalies, resulting in platform-wide bans. Professional advice: Define safety SLOs, like maximum daily requests, and enforce personalization to stay under radar.
To mitigate:
- Mimic human patterns with randomized timing.
- Regularly audit OAuth apps for risks.
- Use cloud integrations for real-time alerts.
Our platform integrates anomaly-aware automation, helping you avoid these pitfalls while scaling outreach. Ready to enhance your setup? Book a Demo or visit GetSales.io.
FAQ
What are account anomaly detection systems primarily used for in sales automation? They identify unusual patterns in LinkedIn activity to prevent bans, ensuring safe, high-volume outreach for B2B teams.
How can I implement anomaly detection for my LinkedIn rental service? Start with rule-based monitoring and integrate ML tools; our Unified Inbox and analytics provide built-in safeguards.
What regulations apply to these systems? Frameworks like NIST and the EU AI Act guide their use for cybersecurity and privacy compliance.
Are there statistics on ban rates without anomaly detection? Yes, unchecked automation can lead to 50% higher restriction rates, per industry benchmarks from sources like Forrester.
How does GetSales.io enhance anomaly detection? We use Single Session Protection and real-time analytics to monitor and rotate activities, keeping your accounts 10x safer.

